Thursday, May 28, 2009
Sunday, May 10, 2009
Is Strategy top of Mind
I recently read a few blogs from Jonathan D. Becher and it reminded me of a couple of stories. I did a couple of webinars a year or so ago with the lead in being a question about how well do you know your corporate strategies. What I consistently found was that 80%+ of the respondants could not cite the strategy off the top of their head. This is clearly not new research as their are a number of people/companies that cite very similar numbers.
I think there are a number of factors at play here:
- Corporate Strategy has no lasting communication vehicle. It is often discussed in conference calls and writen on walls, but we have no effective, living tool. We need to build a communication plan around articulating strategy. Here is a reference to an older blog of mine on Strategy Maps that touches on this subject.
- We often lack a consistent framework for Strategy (or a single version of the truth), so we end up with a number of different frameworks for defining strategic objectives. Corporate uses one framework, the business units another, and then each department creates something new as well. What we end up with is too many messages and no clarity into priorities. All of this becomes to difficult for anyone person to understand, so they just go about their day doing the things that want to do or that are easy to do.
- We also have unstated strategic objectives, or as Oski refers to them in a comment on this blog post, "shadow strategies" where the organization says one thing, but actually does another.
- There is also personal politics and empire building that is probably more widely used than anyone would care to admit. I have seen too many examples where people talk more about how big their team is than provide the value their team creates. If this is what is top of mind, it is probably an indicator of their motivation.
- We don't have a strategy management process. Strategy is done independently from budget, or we hire some consulting firm to develop it and then the binders and reports are placed in an archive.
Tuesday, May 5, 2009
Measuring Anything
I recently read a book entitled How to Measure Anything - Finding the Value of Intangibles in Business by Douglas W. Hubbard. This was an excellent book and helped me to think about how I could measure ANYTHING and how, when necessary to think about how I estimate values. There are some great exercises to stretch your brain in here.
I hear from my OEM's quite often that they can't measure things because they are too complex to calculate. Think about a Security Vendor. How can they measure Risk Exposure? There's nothing in their database that is called Risk Exposure. How can a CRM vendor measure Campaign Effectiveness? How does a Higher Education vendor measure Educator Effectiveness? These are not simple calculations of x+y=z. But they could be easily calculated or estimated within ranges.
Risk Exposure may be calculated by evaluating the trend (not necessarily the actual #) of several things, including Security Threats or numbers of Viruses detected, Security Violations by employees such as non-standard equipment or software, Sensitivity of the asset in violation (the CEO having BearShare or Kaazaa is worse than someone in Accounting having Texas Hold 'em), Value of the asset in violation (the email server vs. one of 100 print servers), etc. All of these things combined can give you some sense of what your Risk Exposure is. You may not have a value of Risk Exposure = 123.53, but you may be able to determine a Risk Exposure of High, Medium or Low which could be backed up by all the specific metrics which go into the calculation.
To demonstrate that truly Anything can be measured. I found this website which calculated some pretty difficult things to measure, the Seven Deadly Sins: Greed, Envy, Wrath, Lust, Gluttony, Sloth and Pride. Check it out, it is a very interesting read - http://scienceblogs.com/gnxp/2009/05/map_of_seven_deadly_sins.php.
ISV's and BPO's need to think about why people buy their software and how can they measure the Effectiveness of their software, not necessarily the Efficiency, see the blog post Effectiveness vs. Efficiency. I highly recommend picking up the book above and reading through it. Then, schedule some time to review your partner's or prospect's website and literature. Pick out 3-5 things that they say they do for their customers. Then, think about how you would measure that? Avoid looking for things like "We can process 1 kazillion transactions per second...". That provides little or no value to their client. Look for the true Value Statements.
I like what I heard from a Higher Education vendor the other day, when they told me "We help Teachers Teach Better and Students Learn Better". Ok, how can you prove that? How do you measure Teacher Effectiveness and Student Learning Ability? Is it strictly by grades? What about drop-out rates? What about student Engagement? What about class participation?
Thursday, April 30, 2009
People do what they want or like to do
If you describe your job or one of your employees jobs as like drinking from a firehose (which seems like all roles these days) chances are you need to be very proactive in determining priorities.
Wednesday, April 29, 2009
Beyond the Checkbox - Part IV
Chris Tyler from Cognos will be joining us for a series of Blogs focused on driving performance for ISVs and OEMs. We will be publishing his Blogs on Thursdays for the next four weeks. Chris is a subject matter expert on getting his clients to elevate value to their customers.
This is the final part of this series. In Part III, we discussed the typical way vendors address their customers reporting needs, by simply checking the reporting box and delivering little or no value to their customers. Here will discuss a better way.
The customer should word their requirement “Do you have an analytical application which proves your application improves the performance of my organization as it relates to increasing our win rates by 7% year over year, reducing sales cycle times by 13%, and increasing our deal sizes by 5% year over year?” I’m sure the vendor would have a much tougher time checking that box, but, that is what the customer truly needs to know.

Figure 2 – An example of an analytic report which shows the business impact and provides context as to what it means to the business, what else to look for and what to do next.
Most enterprise purchases are fairly significant investments and the vendors are often very willing to present case studies where the return on investment, ROI, is achieved in, say, 14 months. Few vendors can actually prove it with their reporting solutions. If the vendor has gone through the process to measure the ROI and understand how it achieves the ROI, why not take that same thought process and put it into an Analytical Application that can be delivered? These types of analytical applications tend to increase customer satisfaction and stickiness, and become a significant, additional revenue stream.
What should the vendor be doing to deliver the value proof? How can the vendor go Beyond the Checkbox? Here are several ways. All of these should leverage and highlight the intellectual property and knowledge of the customer the vendor has.
Identify the value points
Identify 3-7 reasons why customers should buy your application. These become the value points which translate into metrics. These should be SMART (Specific, Measurable, Actionable, Realistic and Time-based).
Domain | Value Statements | SMART Metrics |
CRM |
|
|
Security |
|
|
Human Capital Management |
|
|
Define the metrics
Build a business glossary to define the metric. This should contain what we refer to as the “What?, Why?, So What?, Now What?” This should be able to explain the intent of the metric. All metrics should relate somehow back to the value points identified earlier. If they don’t, there is typically no reason to track it.
Setting targets
The vendor should allow the customer to set targets for the various metrics and if applicable, any tolerances which may be acceptable. Comparing the actual values from the transactional data to the targets set by the customer, allows the user to see if they are on the right track to achieve their results.
Simplify taking action
There may be a need to share the content with another user, a user may want to comment on the performance, there may need to be some action plan set in motion to improve the performance, a user may want to subscribe to the content, or there may be a need to drill into the detail behind the metric.
Content should be in context
Content in context can imply that it is related to the logged in user or is specific to the current view within the vendor’s application. There are a variety of ways to accomplish this ranging from a tight API-level integration to a loosely-coupled web-based integration using URL’s, all depending on the capabilities of the vendor application.
About the author
Chris Tyler has been working for the past 4+ years with Independent Software Vendors (ISV’s) and Business Process Outsourcers (BPO’s) to help them address the specific needs of embedding BI into their platforms. He has seen some great successes and some dismal failures. Some commonalities with the successes are that the vendor delivering the application actually put some thought and intellectual property into their content. The failures typically did not.
Monday, April 27, 2009
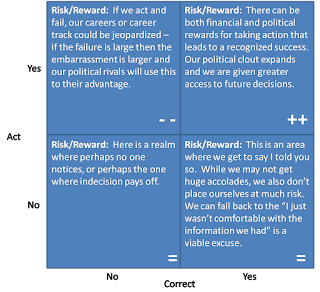
Is a failed action the same as a failure to act?
Wednesday, April 22, 2009
Beyond the Checkbox - Part III
Chris Tyler from Cognos will be joining us for a series of Blogs focused on driving performance for ISVs and OEMs. We will be publishing his Blogs on Thursdays for the next four weeks. Chris is a subject matter expert on getting his clients to elevate value to their customers.
This is Part III of this series. In Part II we discussed the ways a vendor may choose to address the needs of their customer as it relates to reporting. We will show here, the typical way vendors address that with a reporting solution.
Checking the reporting box
When the vendor provides these basic reporting capabilities, I call this “checking the reporting box”. The vendor is delivering enough reporting functionality to allow them to check a box stating that they provide reporting as part of their application, a common requirement of any company evaluating an enterprise application.
Figure 1 – A common example of a report that allows a vendor to check the reporting box, but which provides little or no value proof.
Having the requirement of reporting included with an application is necessary, but it’s how the requirement checkbox is worded. The checkbox is often phrased “Do you have reporting with your application?” The vendor, providing even the most basic reporting capabilities, can then safely check the box, stating “Yes, we deliver reporting as part of our application”. I don’t intend to imply that this is a negative. Operationally, most of these reports are needed and verify that proper actions are being taken and the application is functioning properly. The customer needs more!
- Their reporting typically does nothing to verify the claims that a vendor makes regarding its solution
- The vendor delivers no intellectual property or thought leadership to serve as a differentiator which leads to more wins and larger deals
- There is little or no charge to the customer for the additional capability and therefore the vendor looks at it as a cost center not as a revenue opportunity
- It does nothing to expand the user community of the vendor’s application within the customer
About the author
Chris Tyler has been working for the past 4+ years with Independent Software Vendors (ISV’s) and Business Process Outsourcers (BPO’s) to help them address the specific needs of embedding BI into their platforms. He has seen some great successes and some dismal failures. Some commonalities with the successes are that the vendor delivering the application actually put some thought and intellectual property into their content. The failures typically did not.

+Copyright.jpg)